10 Biggest Data Breaches of the 21st Century
-
 By Niharika Chaurasia
By Niharika Chaurasia - Published on Dec 18 2024

Introduction to Data Breaches
Data breaches have become a major concern in today’s digital world. They not only impact organizations but also compromise individuals' security and privacy.
As data breaches grow and their devastating financial consequences, it’s important for the individuals and organisations to recognize and learn from 10 biggest breaches of the 21st century.
The statistics represents the severity of this problem:
-An unexpected 33% rise in data breaches between 2018 and 2019 depicts the growing vulnerability of our digital infrastructure.
-In 2020 alone, there were over 1,000 reported data breaches globally, exposing sensitive information and causing widespread damage.
Through the analysis of these significant instances, we can learn a lesson and gain insightful information, which will be helpful for organizations and individuals to improve cybersecurity procedures.
This article covers 10 biggest data breaches of the 21st century, including their wide-ranging effects. In today’s digital environment, data breaches are of major concern because they affect millions of people and businesses throughout the world. These instances will help in learning important lessons to work on cybersecurity practices.
Table of Contents
10 Biggest Data Breaches
1.Yahoo (2013-2014): A Cyber Catastrophe
The Breach
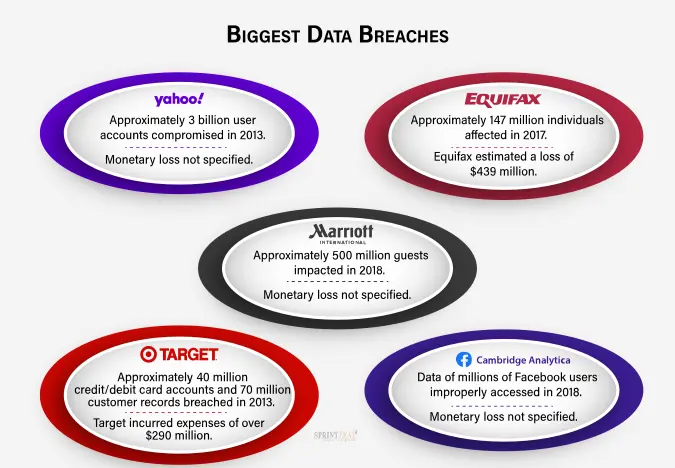
Yahoo data breach is one of the well-known and biggest breaches in history that has affected millions of yahoo user’s account. To unauthorized access to user data, including hashed passwords, email addresses, and names, attackers took advantages of the vulnerabilities.
This breach has brought up serious privacy and data protection concern.
Lessons Learned
- Importance of robust security measures to protect user data.
- Need for prompt detection and response to mitigate the impact of breaches.
- The significance of regular security audits and updates to address vulnerabilities.
2.Equifax (2017): The Great Identity Heist
The Breach
Equifax is one of the top credit reporting agencies which has experienced a significant data breach. The breach has exposed personal information of over 147 million people. Attackers got access of the credit card data, birth dates, and social security numbers by taking advantage of web application vulnerability.
Lessons Learned
- The critical role of vulnerability management and patching in preventing breaches.
- Necessity of comprehensive data protection measures to safeguard personal information.
- The importance of transparency and timely communication with affected individuals.
3.Marriott International (2014-2018): Hospitality Meets Cybercrime
The Breach
Marriott International suffered a prolonged breach that exposed the data of approximately 500 million guests. The attackers gained unauthorized access to the Starwood guest reservation database, compromising personal information, including names, passport numbers, and payment card details.
Lessons Learned
- The significance of thorough due diligence during mergers and acquisitions to identify and address security vulnerabilities.
- Need for continuous monitoring and detection of suspicious activities to mitigate breaches promptly.
- Importance of encrypting sensitive data to provide an additional layer of protection.
4.Target (2013): A Bullseye for Hackers
The Breach
Millions of customers got affected in Target data breach during a busy holiday season. The details of the customer’s credit and debit card got exposed to attackers by gaining access of company’s point-of-sale system. This breach breach highlighted the vulnerability of retailers to cyberattacks.
Lessons Learned
- The importance of secure payment processing systems to protect customer financial data.
- Need for enhanced network segmentation to limit the attackers' lateral movement.
- Significance of continuous employee training to recognize and report potential security threats.

5.Facebook-Cambridge Analytica (2014-2015): A Data Scandal Unveiled
The Scandal
The data breach of Facebook-Cambridge Analytica is known for the unauthorized collection of personal information from millions of Facebook users. This incident shed light on the exploitation of social media platforms for political purposes and raised concerns about user privacy and consent.
Lessons Learned
- The need for robust privacy policies and strict data access controls.
- Importance of user consent and transparency regarding data collection and usage.
- The significance of regular audits to ensure compliance with privacy regulations.
6.MyFitnessPal (2018): Fitness Tracking Turned Compromised
The Breach
A well-known fitness and nutrition app MyFitnessPal were impacted by a data breach where around 150 million users got affected. The unauthorized access of the hashed passwords, usernames, and email addresses were gained by the attackers. This breach underscored the vulnerability of health-related platforms and the value of personal data.
Lessons Learned
- The importance of implementing strong password policies and multi-factor authentication.
- Need for encryption and secure storage of user credentials to mitigate the impact of breaches.
- Significance of proactive threat intelligence to detect and respond to data breaches promptly.
7.LinkedIn (2012): A Professional Network Unraveled
The Breach
LinkedIn, the professional networking platform, experienced a data breach where approximately 167 million user login credentials were exposed. This incident highlighted the importance of protecting user account information and the potential consequences of weak security practices.
Lessons Learned
- The significance of secure password storage mechanisms, such as hashing and salting.
- Need for regular password updates and discouraging password reuse.
- Importance of educating users about strong password practices and potential risks.
8.eBay (2014): Auctioning Off Customer Data
The Breach
eBay, the popular online marketplace, suffered a data breach that compromised personal information of approximately 145 million users. Attackers gained unauthorized access to names, addresses, and encrypted passwords. This breach emphasized the need for comprehensive security measures in e-commerce platforms.
Lessons Learned
- The importance of implementing strong encryption methods to protect user data.
- Need for robust intrusion detection and prevention systems to identify and mitigate attacks.
- Significance of implementing security controls throughout the development and maintenance of web applications.
9.Sony PlayStation Network (2011)
The Breach
The Sony PlayStation Network breach exposed personal and financial information of approximately 77 million users. Attackers gained unauthorized access to the network, leading to a significant disruption of service and compromised customer data.
Lessons Learned
- The importance of regular security assessments and penetration testing to identify vulnerabilities.
- Need for segregation of sensitive data to minimize the potential impact of breaches.
- The significance of incident response planning to minimize downtime and restore services promptly.
10.Anthem (2014): Medical Records Under Siege
The Breach
Anthem is the biggest health insurance providers in the United States, experienced a major data breach that has exposed the personal data of almost 78.8 million people. Through unauthorized access, attackers gained access of the name, social security numbers, and healthcare identity numbers.
Lessons Learned
- The importance of encryption and strong access controls to protect sensitive healthcare data.
- Need for employee training to recognize and report potential security incidents.
- Significance of regular security audits and assessments to ensure compliance with industry regulations.
Understanding the Consequences of Data Breaches
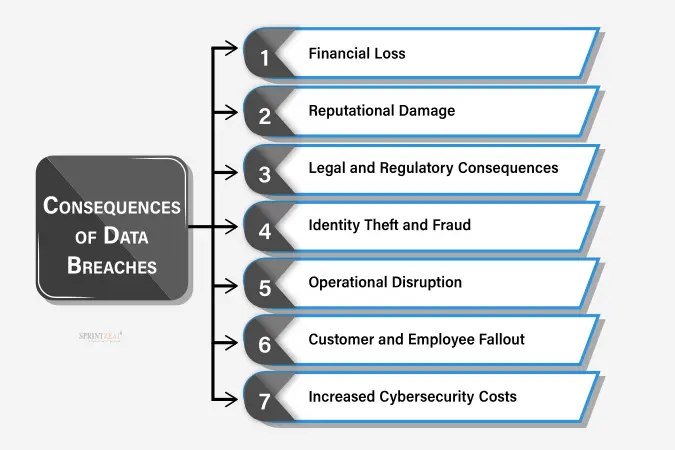
Financial Loss
- Data breaches can result in significant financial losses for organizations, including expenses related to incident response, legal fees, regulatory fines, and potential lawsuits.
Reputational Damagea
- Data breaches can severely damage an organization's reputation, leading to a loss of customer trust and loyalty. It requires lot of efforts and time to rebuild the trust if customers face such situations.
Legal and Regulatory Consequences
- Organizations that experience data breaches may face legal and regulatory consequences, including potential violations of data protection laws and compliance requirements.
Identity Theft and Fraud
- Data breaches often expose sensitive information, such as personal and financial data, which can be used by cybercriminals for identity theft and fraud.
Operational Disruption
- Recovering from a data breach can cause operational disruptions, as organizations need to allocate resources to investigate and remediate the breach, potentially impacting their day-to-day operations.
Customer and Employee Fallout
- Data breaches can lead to customer and employee dissatisfaction, as individuals may feel their personal information is compromised. This can result in a loss of business and talent for the affected organization.
Increased Cybersecurity Costs
- Following a data breach, organizations may need to invest in enhanced cybersecurity measures and technologies to prevent future incidents, resulting in increased expenses.
- Remember, taking proactive measures to protect data and strengthen cybersecurity defenses is crucial in mitigating the impact of data breaches.
Conclusion
As the data breaches are increasing in 21st century, many organizations and individuals are getting affected. We can gain valuable insights into the vulnerabilities and consequences by closely examining these 10 biggest data breaches of 21st century.
To mitigate the risk of future breaches its essential to have a strong cybersecurity measures, including data encryption, vulnerability management, and providing training to the employees of the organization.
In this digital age, to protect ourselves and our organization, its crucial to stay informed and proactive towards potential cyber threats and breaches.
At Sprintzeal, we understand the significance of data security and offer a range of training and certification programs designed to equip professionals with the knowledge and skills needed to safeguard sensitive information.
Sprintzeal courses are aimed to improve your skills and provide you the ability to make a difference. Whether you are an experienced professional or just beginning your professional career, our tailored cybersecurity courses helps in enhancing skills and make a meaningful impact.
Visit the Sprintzeal blog to explore more articles on cybersecurity, data breaches, and industry trends. Together, let's build a secure digital future. Join us today!
Subscribe to our Newsletters
Popular Programs
CISSP® - Certified Information System Security Professional
Live Virtual Training
- 4.1 (964 + Ratings)
- 5k + Learners
CISA® - Certified Information System Auditor
Live Virtual Training
- 4.8 (426 + Ratings)
- 42k + Learners
CISM® - Certified Information Security Manager
Live Virtual Training
- 4.7 (200 + Ratings)
- 69k + Learners
CCSP® - Certified Cloud Security Professional
Live Virtual Training
- 4.3 (964 + Ratings)
- 32k + Learners
Trending Posts
Guess What Google Did When a Employee Breached Their Firmware
Last updated on Dec 24 2024
How JPMorgan Chase Strengthened Security After Facing Cyber Threats
Last updated on Jan 24 2025
Ethical Hacking Career: A Career Guide for Ethical Hacker
Last updated on Dec 20 2022
Dropbox Data Breach: What Companies Can Learn from It
Last updated on Jan 9 2025
Cybersecurity Interview Questions and Answers 2026
Last updated on Sep 8 2025
How Does Slack Respond to Security Challenges?
Last updated on Dec 20 2024
Categories
- Other 72
- Agile Management 48
- Cloud Computing 57
- Project Management 174
- Big Data 67
- Business Management 88
- Digital Marketing 81
- IT Service Management 29
- Programming Language 59
- AI and Machine Learning 85
- IT Security 113
- Quality Management 78
- IT Hardware and Networking 26
- Microsoft Program 5
- Workplace Skill Building 14
- Risk Management 9
- Information Security 8
- Leadership and Management 9
- Corporate Training and Development 1
Trending Now
Top 5 Compelling Reasons To Get A Cyber Security Certification
ebookHow to Become IT Security Expert with CISSP Certification
ebookTop 20 Reasons You Should Get a CISSP Certification
ebookWhat is CISSP? – Everything about CISSP Certification Explained
ebookPass CISSP Exam - How to Clear CISSP Exam in First Attempt 2026 (UPDATED)
ebookCISSP Certification – Top 25 Career Benefits in 2026
ebookCybersecurity – Everything You Need to Know About it
ebookUpdated Google Certification Training Course list 2026
ArticleWhich Certification is best for Cybersecurity?
ebookWhich Cybersecurity Certification Should I Get First?
ebookCysa+ certification – Should you get it?
ebookList of Top Security Certifications
ArticleEasiest Security Certification to Get
ebookCISM certification cost and career benefits
ebookCybersecurity Fundamentals Explained
ebookISACA Certifications List 2026
ebookCareer Benefits of CISM Certification in 2026
ArticleList of Top Information Security Certifications in 2026
ebookCISM certification cost details
ArticleMitigate the Cyber-Attack Risks with Best Cyber Security Protocols
ebookCybersecurity Interview Questions and Answers 2026
ebookTop Cybersecurity Software Tools In 2026
ebookInformation Security Analyst - Career, Job Role, and Top Certifications
ebookCyber Security Analyst - How to Become, Job Demand and Top Certifications
ebookWhat is Data Security - Types, Strategy, Compliance and Regulations
ebookData loss Prevention in Cyber Security Explained
ebookCybersecurity Controls Explained in Detail
ebookCybersecurity Framework - A Complete Guide
ebookWhat is Cryptography - A Comprehensive Guide
ebookData Leak - What is it, Prevention and Solutions
ebookCybersecurity Career Paths Guide
ebookFuture of Cybersecurity - Trends and Scope
ebookCyber Security Careers and Outlook - 2026 Guide
ebook5 Cybersecurity Predictions in 2026 - Trends and Challenges
ebookScope for Cybersecurity in 2026 - Latest Update
ebookEthical Hacking Career: A Career Guide for Ethical Hacker
ebookApplication Security: All You Need To Know
ebookCybersecurity Roles - Top Roles and Skills to Consider in 2026
ebookHow to Get Cyber Essentials Certified
ebookTop 10 Cyber Security Threats and How to Prevent Them
ebookTop 10 Network Scanning Tools of 2026
ebookCyber Incident Response Plan: A Comprehensive Guide
ebookInformation Assurance Careers - Exploring Career Paths
ebookWhat is the Department of Defense (DoD) Directive 8140
ebookCybersecurity Mesh Architecture: What It Is and How to Build It
ebookWhat is Threat Modeling? Methodologies, Types, and Steps
ebookWhat is Digital Forensics? Types, Process & Challenges
ebookInformation Assurance Model in Cybersecurity
ebookHow to Become an Information Security Analyst Salary, Skills, and More
ArticleList of Top Department of Defense (DoD) Approved 8570 Certification Courses
ebookTop 5 Ransomware Attacks to Watch Out for in 2026
ebookJob Prospects for DoD Certified Professionals: A Pathway to Success in cybersecurity
ebookWhat is a Cybersecurity Incident?-Types, Impact, Response Process and More
ebookCyber Security Planning - A Detailed Guide for Risk Mitigation
ebookWhat is Cybercrime? Exploring Types, Examples, and Prevention
ebookRecent Cyber Attacks & Data Breaches in 2026
ebookCybersecurity Strategy: Building a Strong Defense for Business
ebookCybercrime Impacts On Business: 6 Major Effects
ebook5 Types of Cyber Attacks You Should Be Aware of in 2026
ebookCloud Cyber Attacks: Causes, Types, Prevention and Protection
ebookCloud Malware: Types of Attacks and Security Measure
ebookCyber Attack Statistics and Trends to Know in 2026
ebookList Of Top Cybersecurity Threats In 2026
ebookSafeguarding Digital Domain: 10 Most Common Cybercrimes
ebookDemystifying Cloud-Based Cyber Attacks: A Comprehensive Guide
ebookPrevent Cyber Attacks: Strategies to Protect Your Digital Assets
ebookList of Top 10 Cybersecurity Careers in 2026
ebookTop 20 Cybersecurity Trends to Watch Out for in 2026
ArticleHow to Become Cybersecurity Engineer
ArticleUnderstanding Risk assessment in audit planning
ArticleFundamentals of Risk-Based Auditing: A Strategic Framework
ArticleRisk-based Audit Planning Guide for Beginners
ebookTop 8 Types of Cybersecurity Jobs and Salary Insights
ArticleA Comprehensive Guide to Building Risk-Based Internal Audit Plan
ArticleRisk-Based Internal Auditing Approaches: 7 Steps to Explore
ArticleCompTIA Security+ 601 vs. 701: Understanding Key Differences
ArticleWhy and How to Perform a Risk-Based Internal Audit
ArticleRisk-Based Auditing Techniques Explained
ebookEvolving Cyber Threats and Vulnerabilities in Cybersecurity Risk Management
ArticleWhat Is Secure Access Service Edge (SASE)?
ArticleHow to Stay Cyber-Secure in Work and Personal Life (Tips and Practices)
ArticleIBM Data Breach: Is IBM Really Breach-Proof?
ArticleTarget Cyber Attack: Key Lessons from the 2013 Data Breach
ArticleLinkedIn User Data Protection Explained
ArticleCanva Data Breach: Best Lessons for Users and Businesses
ArticleHow Did Capital One Respond to Their Major Cyber Incident?
ArticleWhat Innovative Measures Did Reddit Take to Protect User Data?
ArticleHow Does Slack Respond to Security Challenges?
ArticleTwitch Data Breach: Response, Changes, and Key Takeaways
ArticleGuess What Google Did When a Employee Breached Their Firmware
ArticleEthical Hacking Tools: Best Ones for Cybersecurity in 2026
ArticleWhat Happened When Cisco Faced a Cyber Incident?
ArticleWhat Sony Did to Rebuild Trust After a Major Cyberattack
ArticleHow to Handle a Data Breach? Learn from Microsoft!
ArticleCybersecurity Mesh: A New Approach for Security Design
ArticleHow Target Turned a Cyber Crisis into a Lesson for All
ArticleDropbox Data Breach: What Companies Can Learn from It
ArticleHow JPMorgan Chase Strengthened Security After Facing Cyber Threats
ArticleThe Future of Online Security: Trends to Watch in 2026
ArticleLatest Trends in CyberSecurity
ArticleTop 12 Cyber Security Apprenticeships with High Earning Potential in 2026
ArticleEnhancing Safety and Competence in Today's Workplace
ArticlePrivacy at Your Fingertips: How iPhone Users Can Use Tools Securely
ArticleAge Matters: Understanding the Generational Gap in Online Safety Education
ArticleCybersecurity 101: Why Cybersecurity is the Hottest Career Right Now
ArticleWhy Cybersecurity Training Should Be Part of Every Professional's Career Plan
ArticleHow to Protect Your Data When Traveling to Countries Like Malaysia?
ArticleTop Online Master's in Cybersecurity Programs for Working Professionals
ArticleHow AI Detectors Strengthen Cybersecurity in Modern Networks
ArticleHow to Become a Cybersecurity Engineer: Step-by-Step Career Guide
ArticleWhy Certification in Risk and Compliance Is Critical in Today’s Financial World
ArticleWhat is OSI Model? - Layers of OSI Model
Article



















