How to Get Cyber Essentials Certified
-
 By Niharika Chaurasia
By Niharika Chaurasia - Published on Apr 5 2023

Table of Contents
Introduction
In this world of digitalization, information is widely available on the internet, and both businesses and consumers are at risk of data theft.
Every year, as technology becomes more complex, so do cyberattacks. Digital crime is not limited to any single internet-accessible platform. Without cybersecurity, it’s difficult for organizations or consumers to protect their data, devices, network, or system from malicious attacks.
Organizations have to have a "cyber essentials" certification in order to show their credentials as trustworthy and safe in terms of cyber security.
In this article by Sprintzeal, we have discussed all aspects of cyber essentials and their benefits. It also explains how Cyber Essentials works and the necessary steps to become Cyber Essentials Certified.
What is Cyber Essential?
Cyber Essentials is a UK government-backed scheme that was launched in 2014. The aim of the scheme was to provide basic cyber security for organizations of any size.
The main purpose of cyber essentials is to protect organizations from common cyber threats, such as hacking, phishing, and malware.
Cyberattacks can be of low to high impact, but the vast majority are very basic in nature and are conducted by unskilled individuals. They are the digital version of a thief trying to infiltrate your system from the main access point.
Cyber Essentials assists organizations in improving their overall state of security by providing a framework for implementing and maintaining effective security measures.
What is Cyber Essentials Certification?
A cyber essentials certification is a cyber security certification program that equips businesses with the tools they need to protect their systems and customer data.
The National Cyber Security Centre (NCSC) oversees the certification, which requires organizations to complete a self-assessment questionnaire covering five important technical controls, which we will discuss in another section.
Furthermore, with the basic level of protection against cyber threats, Cyber Essentials certification also helps organizations fulfill industry regulations and standards. For instance, as part of their regulatory obligations, businesses that handle sensitive information, such as financial information or personal data, may be required to show their cyber security measures.
With Cyber Essentials certification, an organization can prove that it has taken the necessary steps to protect its IT and systems.
To prevent these attacks from happening, there are 2 levels of certification, which are essential for the organization to protect themselves against the growing threat of cyber-attacks and help in declaring the basic controls that the organization should have in place to protect themselves.
Cyber Essentials
-It’s a foundation-level certification.
-designed to provide a declaration of the basic controls your organization should have in place to diminish the risk from common cyber threats.
-Prevents most common attacks.
Cyber Essentials Plus
-It is the highest level of certification offered under the Cyber Essentials scheme.
-It is a more difficult test and technical verification for your organization’s cyber security systems.
-In Cyber Essentials Plus, vulnerability tests are carried out to ensure your organization is protected against common hacking and phishing attacks.
These certifications outline a focused set of controls that offers clear guidance on basic cybersecurity for organizations and provides a complete foundation of cybersecurity measures that any organization can implement with little investment.
How do Cyber Essentials Work?
With the implementation of 5 key controls in Cyber Essentials, organizations can protect themselves from the most common cyberattacks.
The controls for cyber essentials include:
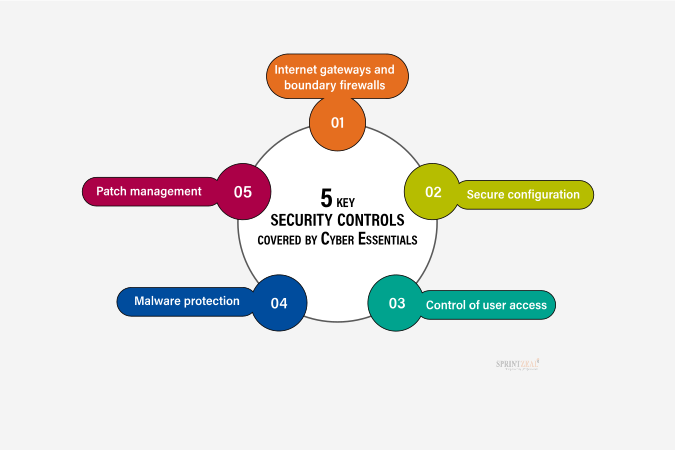
Organizations can self-assess their compliance with the scheme. It’s mandatory to complete a questionnaire covering the five essential controls.
Once certified, organizations can display the cyber essentials logo to show their commitment to cyber security.
Why Become Cyber Essentials Certified?

-According to the National Cyber Security Center, by taking the Cyber Essentials certification process into consideration and implementing even one of the five controls of Cyber Essentials, an organization can provide protection to the organization from cyberattacks up to 80%.
-As per the Cyber Security Breaches Survey 2020 reports, the pattern and tactics of cyberattacks have changed over the past year. The cyber hackers are becoming more skilled and have evolved to a variety of counter-hacking methods.
-Assure customers that the organization is working to protect data and IT from cyber-attacks.
-Provides a clear image of the cyber security level of an organization.
-To get Government contracts, its necessary to be cyber essentials certified organization.
-Attract new business with the promise you have cyber security measures in place.
-Cyber Essentials certification specifies that an organization takes a proactive stand against malicious cyber-attacks.
How to get Cyber Essentials Certified?
The process of Cyber Essentials certification includes the following steps:

1) Preparation for the certification process
-Preparation for the certification process includes readiness for cybersecurity.
-Organizations should ensure that they have the required resources and systems in place before beginning the certification process.
-Process may include changes to existing security measures such as updating software, patching vulnerabilities, and implementing appropriate access controls.
-An overview of the system and an action plan based on the actual Cyber Essentials Questionnaire are provided.
2) Self-assessment questionnaire
-Self assessment questionnaire is the very first step to get cyber essentials certified.
-This step covers five areas of technical control (boundary firewalls and internet gateways, secure configuration, access control, malware protection, and patch management).
-Organisations are required to answer questions about their current cybersecurity measures and provide evidence to support their answers.
3) External assessment
-After the self-assessment questionnaire, an external assessment is performed.
-An independent certification body will review responses and conduct a vulnerability scan on the organization's systems.
-The certification body will then verify that the organization has fulfilled the required standards and, based on their evaluation, will award the certification.
4) Implement suggested improvements
-Any fault identified by the certification body in the organization's security measures, will be recommended for improvement.
-To keep their Cyber Essentials certification, organizations must implement these recommendations within a specific timeframe.
5) Annual certification
-Once Cyber Essentials is certified, it must be kept current by renewing it annually.
-To keep their security measures up to date and effective, organizations must take the self-assessment questionnaire and undergo a new external assessment each year.
Cost of Cyber Essentials Certification
For any organization, becoming Cyber Essentials Certified includes several costs, such as
- cost of preparing for the certification process
This may differ from organization to organization. The cost may vary depending on the size of the organization and the level of its existing security measures.
- cost of the self-assessment questionnaire and external assessment
It can range from a few hundred to several thousand pounds, which also depends upon the certification body, size, and complexity of the organization.
- cost of implementing any recommended improvements
This depends upon the weakness/fault identified by the certification body, the nature of the recommendation, and the resources required to implement it. For example, implementation includes the purchase of hardware and software to strengthen the security system of the organization.
Pricing Guide provided by NCSC:
Micro organisations (0-9 employees)- £300 + VAT
Small organisations (10-49 employees)- £400 + VAT
Medium organisations (50-249 employees)- £450 + VAT
Large organisations (250+ employees)- £500 + VAT
Eventually, organizations must take the cost of maintaining their cyber essentials certification into consideration. The cost also includes the renewal of the certification each year and the implementation of necessary changes to security measures.
The Bottom Line
At last, Cyber Essentials certification plays a significant role in the overall functioning of the organization. Becoming Cyber Essentials Certified is a straightforward process if the IT infrastructure of the organization is maintained properly.
Both Cyber Essentials and Cyber Essentials Plus are equally beneficial in terms of cyber-attack protection; however, if your organization requires a more in-depth audit of critical controls, Cyber Essentials Plus comes in handy.
For any organization, it’s important to ensure cybersecurity practices to protect businesses against any kind of cyberattack. Hence, cybersecurity professionals play a vital role in protecting sensitive data and digital information.
With Sprintzeal cybersecurity courses, you can take your career on a progressive path. Our industry-leading training and internationally recognized certifications can help you stand out from others. Visit Sprintzeal's all-courses page for more career-enhancing courses.
For more interesting blogs, visit the Sprintzeal blog page, and click here for any course-related query, or to connect with us.
Read more blogs
Cybersecurity Roles - Top Roles and Skills to Consider in 2023
Cyber Security Analyst - How to Become, Job Demand and Top Certifications
Subscribe to our Newsletters
Popular Programs
CISSP® - Certified Information System Security Professional
Live Virtual Training
- 4.9 (964 + Ratings)
- 43k + Learners
CISA® - Certified Information System Auditor
Live Virtual Training
- 4.8 (426 + Ratings)
- 66k + Learners
CISM® - Certified Information Security Manager
Live Virtual Training
- 4.2 (200 + Ratings)
- 33k + Learners
CCSP® - Certified Cloud Security Professional
Live Virtual Training
- 4.8 (964 + Ratings)
- 57k + Learners
Trending Posts
Which Certification is best for Cybersecurity?
Last updated on Dec 16 2022
CISM certification cost and career benefits
Last updated on Aug 3 2022
What Happened When Cisco Faced a Cyber Incident?
Last updated on Dec 26 2024
Cyber Security Planning - A Detailed Guide for Risk Mitigation
Last updated on Jul 19 2023
Target Cyber Attack: Key Lessons from the 2013 Data Breach
Last updated on Dec 9 2024
Application Security: All You Need To Know
Last updated on Dec 20 2022
Categories
- Agile Management 54
- AI and Machine Learning 42
- Big Data 53
- Business Management 51
- Cloud Computing 44
- Digital Marketing 56
- Information Security 8
- IT Hardware and Networking 17
- IT Security 103
- IT Service Management 29
- Leadership and Management 1
- Microsoft Program 2
- Other 43
- Programming Language 31
- Project Management 162
- Quality Management 75
- Risk Management 8
- Workplace Skill Building 2
Trending Now
Which Certification is best for Cybersecurity?
ebookTop 5 Compelling Reasons To Get A Cyber Security Certification
ebookHow to Become IT Security Expert with CISSP Certification
ebookTop 20 Reasons You Should Get a CISSP Certification
ebookCISM certification cost and career benefits
ebookWhat is CISSP? – Everything about CISSP Certification Explained
ebookPass CISSP Exam - How to Clear CISSP Exam in First Attempt 2024 (UPDATED)
ebookCISSP Certification – Top 25 Career Benefits in 2024
ebookCybersecurity – Everything You Need to Know About it
ebookCybersecurity Strategy: Building a Strong Defense for Business
ebookCyber Attack Statistics and Trends to Know in 2024
ebookUpdated Google Certification Training Course list 2024
ArticleWhich Cybersecurity Certification Should I Get First?
ebookCysa+ certification – Should you get it?
ebookList of Top Security Certifications
ArticleEasiest Security Certification to Get
ebookCybersecurity Fundamentals Explained
ebookISACA Certifications List 2024
ebookCareer Benefits of CISM Certification in 2024
ArticleList of Top Information Security Certifications in 2024
ebookCISM certification cost details
ArticleSafeguarding Digital Domain: 10 Most Common Cybercrimes
ebookMitigate the Cyber-Attack Risks with Best Cyber Security Protocols
ebookCybersecurity Interview Questions and Answers 2024
ebookData Leak - What is it, Prevention and Solutions
ebookTop Cybersecurity Software Tools In 2024
ebookWhat is Cryptography - A Comprehensive Guide
ebookInformation Security Analyst - Career, Job Role, and Top Certifications
ebookCyber Security Analyst - How to Become, Job Demand and Top Certifications
ebookIBM Data Breach: Is IBM Really Breach-Proof?
ArticleWhat is the Department of Defense (DoD) Directive 8140
ebookInformation Assurance Model in Cybersecurity
ebookWhat is Data Security - Types, Strategy, Compliance and Regulations
ebookData loss Prevention in Cyber Security Explained
ebookCybersecurity Controls Explained in Detail
ebookCybersecurity Framework - A Complete Guide
ebookCybersecurity Career Paths Guide
ebookFuture of Cybersecurity - Trends and Scope
ebookScope for Cybersecurity in 2024 - Update for 2024
ebookCyber Security Careers and Outlook - 2024 Guide
ebook5 Cybersecurity Predictions in 2024 - Trends and Challenges
ebookEthical Hacking Career: A Career Guide for Ethical Hacker
ebookApplication Security: All You Need To Know
ebookCybersecurity Roles - Top Roles and Skills to Consider in 2024
ebookTop 10 Cyber Security Threats and How to Prevent Them
ebookTop 10 Network Scanning Tools of 2025
ebookCyber Incident Response Plan: A Comprehensive Guide
ebookInformation Assurance Careers - Exploring Career Paths
ebookCybersecurity Mesh Architecture: What It Is and How to Build It
ebookWhat is Threat Modeling? Methodologies, Types, and Steps
ebookWhat is Digital Forensics? Types, Process & Challenges
ebookRecent Cyber Attacks & Data Breaches in 2024
ebookHow to Become an Information Security Analyst Salary, Skills, and More
ArticleList of Top Department of Defense (DoD) Approved 8570 Certification Courses
ebookTop 5 Ransomware Attacks to Watch Out for in 2024
ebookJob Prospects for DoD Certified Professionals: A Pathway to Success in cybersecurity
ebook10 Biggest Data Breaches of the 21st Century
ebookWhat is a Cybersecurity Incident?-Types, Impact, Response Process and More
ebookCyber Security Planning - A Detailed Guide for Risk Mitigation
ebookWhat is Cybercrime? Exploring Types, Examples, and Prevention
ebookCybercrime Impacts On Business: 6 Major Effects
ebook5 Types of Cyber Attacks You Should Be Aware of in 2024
ebookCloud Cyber Attacks: Causes, Types, Prevention and Protection
ebookCloud Malware: Types of Attacks and Security Measure
ebookList Of Top Cybersecurity Threats In 2024
ebookRisk-based Audit Planning Guide for Beginners
ebookDemystifying Cloud-Based Cyber Attacks: A Comprehensive Guide
ebookPrevent Cyber Attacks: Strategies to Protect Your Digital Assets
ebookList of Top 10 Cybersecurity Careers in 2024
ebookTop 20 Cybersecurity Trends to Watch Out for in 2024
ArticleHow to Become Cybersecurity Engineer
ArticleUnderstanding Risk assessment in audit planning
ArticleFundamentals of Risk-Based Auditing: A Strategic Framework
ArticleTop 8 Types of Cybersecurity Jobs and Salary Insights
ArticleA Comprehensive Guide to Building Risk-Based Internal Audit Plan
ArticleRisk-Based Internal Auditing Approaches: 7 Steps to Explore
ArticleCompTIA Security+ 601 vs. 701: Understanding Key Differences
ArticleWhy and How to Perform a Risk-Based Internal Audit
ArticleRisk-Based Auditing Techniques Explained
ebookEthical Hacking Tools: Best Ones for Cybersecurity in 2025
ArticleEvolving Cyber Threats and Vulnerabilities in Cybersecurity Risk Management
ArticleWhat Is Secure Access Service Edge (SASE)?
ArticleHow to Stay Cyber-Secure in Work and Personal Life (Tips and Practices)
ArticleTarget Cyber Attack: Key Lessons from the 2013 Data Breach
ArticleLinkedIn User Data Protection Explained
ArticleCanva Data Breach: Best Lessons for Users and Businesses
ArticleHow Did Capital One Respond to Their Major Cyber Incident?
ArticleWhat Innovative Measures Did Reddit Take to Protect User Data?
ArticleHow Does Slack Respond to Security Challenges?
ArticleTwitch Data Breach: Response, Changes, and Key Takeaways
ArticleGuess What Google Did When a Employee Breached Their Firmware
ArticleWhat Happened When Cisco Faced a Cyber Incident?
ArticleWhat Sony Did to Rebuild Trust After a Major Cyberattack
ArticleHow to Handle a Data Breach? Learn from Microsoft!
ArticleCybersecurity Mesh: A New Approach for Security Design
ArticleHow Target Turned a Cyber Crisis into a Lesson for All
ArticleDropbox Data Breach: What Companies Can Learn from It
ArticleHow JPMorgan Chase Strengthened Security After Facing Cyber Threats
ArticleThe Future of Online Security: Trends to Watch in 2025
ArticleLatest Trends in CyberSecurity
ArticleTop 12 Cyber Security Apprenticeships with High Earning Potential in 2025
ArticleEnhancing Safety and Competence in Today's Workplace
Article
















