Cybersecurity – Everything You Need to Know About it
-
 By Melissa
By Melissa - Published on Dec 19 2024

Introduction to Cybersecurity
Cybersecurity has become an integral part of every organization, with an even higher scope for cybersecurity in 2023. Data threats faced by any company can damage its chances of growing. The ease and accessibility of online businesses have also resulted in threats from hackers.
In a minute, millions of bytes of data can be stolen. This makes the organization vulnerable and leads to their downfall. Cybersecurity risks are threatening to collapse the IT infrastructure of many companies.
An increasing number of large organizations are doing their business online. The internet revolution has modified our lives and made them better. We can now access everything with a click of a button from the comfort of our homes.
From apparel to medicines, everything can be delivered to our doorsteps through delivery apps and websites. This has led to the growth of many organizations but, at the same time, has attracted threats to security.
There are a plethora of options that you can explore to build a career in cybersecurity. Many individuals get trained prior so that it would become easier for them to get employed in this sector and become cybersecurity consultants.
Table of Contents
Importance of Cybersecurity
According to a study report, nearly 83% of companies around the world face cybersecurity threats daily. Continuous surveillance is necessary to ensure that the IT integrity of a company is maintained.
This can be done by employing highly skilled cybersecurity professionals who will safeguard the software of the company and prevent it from upcoming cyberattacks.
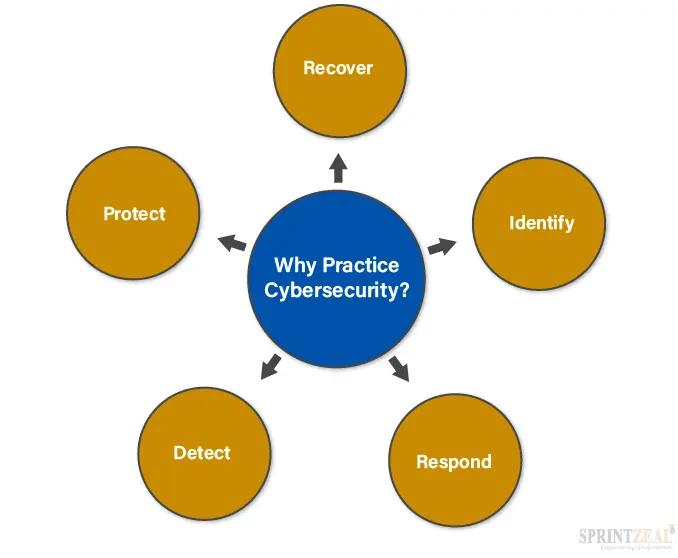
It’s been a staggering rise in the level of cybercrime. Many companies hesitate to invest in cybersecurity. As a result, they face irreversible damage to their IT infrastructure. The online presence of companies makes them increasingly vulnerable to threats and data breaches. This compels many organizations to invest in cyber-security professionals.
Why are Cybersecurity Professionals in High Demand?
Cybersecurity jobs are one of the fastest-growing jobs. Cybersecurity professionals ensure that the company's software stays protected from hackers. They utilize their IT skills to devise foolproof methods for companies using which they can prevent their sensitive data from getting accessed.
In the past, many companies have come under fire from users whose data was breached and leaked. This created a bad reputation for the company and led to enormous losses. This could have been prevented if the companies had invested in skilled cybersecurity professionals. It would have identified the loopholes in their system and devised ways to rectify them.
That traditional trend has been reversed now as a high number of companies are willing to spend millions on cybersecurity. So, if you are interested in taking up a role as a cyber-security professional, this is the best time to do so.
There are plenty of job options available for professionals who want to pursue cybersecurity careers and outlook. The job of a cybersecurity analyst is one of the most coveted roles in this sector. It will help organizations secure their data and create foolproof solutions for their systems.
Role of Cybersecurity in Organizations
Cyberattacks are evolving as an intermittent danger to organizations. Most organizations are facing increasing threats because of their vulnerable states. When you take your business online, it results in a lot of people accessing your software.
Normal users only avail of those services that are available to them, but there are notorious hackers who will find loopholes in your security systems and devise ways to breach past your firewalls.
After doing this, they would be able to access your sensitive data and use it to their advantage. This is a rising trend, and a lot of organizations have lost their reputation because of online attacks.
The hackers, who try to get into the systems of the organizations, are well-equipped with the latest tools. As compared to them, the organizations don’t have the IT support that would help them prevent such attacks.
A recent report showed that only 5% of the files are protected globally. This is a very small amount as compared to the enormous number of files being stolen each second. Hackers are getting smart.
The moment you try to build an effective anti-hack system, they devise newer ways to get past your security wall. Normal people in an organization cannot prevent this attack by themselves. To deal with cybercrimes, an organization needs cybersecurity professionals who would help it to protect its sensitive information from hackers.
Why do cybercrimes occur and how does cybersecurity help?
The main motive behind cybercrimes is stealing the data of innocent and unaware users. If users avail of any services online, the risk of getting attacked by hackers, who will use efficient methods to steal their data without their knowledge.
The majority of cybercrimes are related to hacking. Hacking is a term that is used to define the condition when your software system gets attacked. The hackers breach your firewall by finding a loophole in it.
It is very dangerous as we store large amounts of personal information on our computers.
For larger organizations, cybercrimes are usually related to the stealing of user information. Hackers can even access admin accounts and change the software of the organization, making it impossible for authorities to access their own networks.
An estimated 95% of organizations have faced cybercrimes in some way or another. This is more prevalent in the USA, where increased access to internet facilities has spurred the growth of large cybercriminal gangs.
How is Cybersecurity Implemented?
To safeguard your data from cyberattacks, you need to protect and secure it. Create effective solutions for cybersecurity threats by using the latest cybersecurity software.
Cybercriminals are evolving faster than ever before. This should make you worry because you also need to increase the level of defense. Businesses are at a higher risk nowadays. Their sensitive data might get stolen by attackers who can use the information to extort money from them.
Cybersecurity awareness is required to prevent such large-scale attacks. For that, cybersecurity awareness training is imparted to individuals who are wishing to start a career in cybersecurity.
There are three main domains of cybersecurity infrastructure. Let’s have a look at each of them.
1) IT security:
IT security, or information security, is the protection of data using electronic networks. Cybersecurity is limited to protecting only digital data, but IT security aims to secure both digital and physical data from attackers.
2) Cybersecurity:
The cybersecurity definition is that it protects your digital data from cybersecurity breaches. It is implemented in your computers, PCs, laptops, or other systems that are susceptible to attacks by hackers.
3) Computer security or network security:
Network security or computer security focuses on the in-between areas between hardware and software. When you’re sending information through your computers, the server that you are sending the information to should be the sole recipient of it.
Attackers can intercept your information midway and make changes to it. They can also access it and steal sensitive content.
Computer security uses a combination of both hardware and software to protect the information you are sending.
What are the Categories of Cybersecurity?
There are many types of security based on the type of network it protects. Here are some of the subsets of Cybersecurity.
Infrastructure Security
This focuses on preserving the integrity of cyber infrastructure from any harm. It consists of only cyber-physical systems. A good example of an attack on infrastructure security is the recent shutdown of the US electrical grid system by some notorious hackers.
Network Security
This focuses on protecting the networks from attacks by cybercriminals. Securing internal networks and creating multiple levels of barriers is the only way to prevent network security breaches. Passwords and encryptions are the other methods of protecting against network security breaches.
Application Security
Software applications have increased the chances of getting attacked. To protect these applications, antivirus software is developed.
This antivirus software will protect the applications from getting attacked by malicious firmware. Firewalls and encrypting data are other ways of protecting applications.
Information Security
This is a holistic system of protecting data. It focuses on protecting both physical and digital data from harm. Any unauthorized system is not allowed to access information. Blocking of access is applied aggressively to prevent attackers from hacking into the system.
Cloud Security
Cloud applications have become a new way of storing and accessing data from any part of the world. More people are using cloud services to store their data.
While this is beneficial, it also invites the attention of hackers who find loopholes within the system and breach it using effective modern technologies.
Data Security
Data loss prevention is an integral part of data security. For this, fool-proof policies and processes are invented that will prevent the loss of data. Network permissions can be set to prevent unauthorized access to data.
User Security
The end-users are at the highest risk of getting trapped in a cyberattack. This is because they have little awareness of cybersecurity principles. Creating cybersecurity awareness among users can make them more vigilant and alert to cybersecurity threats.
What are the Different Types of Cybersecurity Threats?
Cybersecurity threats are the attacks that are carried out on your systems. They are of many types depending on their mode of attack and way of breaching past firewalls. Here are some of the types of cybersecurity attacks.
Attack on privacy:
Threats to privacy are the most common type of cybersecurity attack. They are intended to steal your private information and personal details.
Once a hacker accesses your personal information, he/she can use it to extort huge amounts of money from you. It has been the most common type of cybersecurity attack.
Leaking of information:
Often, attackers with the aim to malign your reputation can steal your data and make it public. This is a very dangerous form of attack because it will make you vulnerable and susceptible to weak emotional states. Many people suffer from nervous breakdowns after their personal information gets stolen.
They are blocking access:
Denials of service or DoS attacks are the most common types of attacks in recent times. Hackers prevent organizations or individuals from accessing their data by changing the security framework of their systems.
This can halt the businesses of large companies. So, instead of reporting to the authorities, many companies pay large amounts to hackers and secure their networks afterward.
What are Malware and Ransomware?
Malware can be defined as malicious software (hence the name). This is a pre-planned attack on the security of an organization. It will lead to the blocking of access by hackers as a result of which the authorities will not be able to access their own data. Malware can breach the security systems of the people who receive them.
They often come in the form of suspicious file that contains software that will steal your data without your knowledge. Viruses and worms are a type of malware.
Ransomware is also a type of malware, but, in the case of ransomware, data is stolen with the purpose of extorting money. The attackers hold your data with them and do not release it until you pay them a large sum of money.
These attacks are mainly aimed at sensitive and important information that is very important to the owner. If the money is not paid within the stipulated time, the user might lose access to it forever.
What is the Extent of Cybersecurity Threats?
Cybersecurity threats are fast evolving. From malicious firmware to viruses and worms, cyber attackers are leaving no stone unturned to make sure that you have a tough time online.
The cybersecurity threat is subdivided into 3 categories, cybercrime attacks, cyberattacks, and cyberterrorism. All three types of attacks are equally dangerous, but their extent and scale of reach vary.
Cybercrime
This is carried out against individuals, and the attack targets your personal computer network and system. The motive behind this type of attack is gaining money through extortion.
Cyberattack
These types of attacks are carried out against organizations and are aimed at collecting and revealing private information.
Cyberterrorism
This is the most dangerous form of cyberattack and targets an entire country or a particular geographical area. The motive behind this kind of attack is not money. Individuals indulging in cyberterrorism do so to spread fear and panic.
They can also carry out these attacks to steal sensitive information like defense plans of countries.
Protection Against Cybersecurity Attacks
Merely spreading awareness about cybersecurity attacks is not enough. Active vigilance and alertness are required to protect yourself and your organization from cyber threats.
Cybersecurity blogs and courses do an amazing job of making people aware of cybersecurity threats. Cybersecurity companies and cybersecurity businesses are coming up with innovative solutions to protect individuals and organizations against cyberattacks. Cybersecurity awareness is crucial for improving cybercrime rates.
There are different ways of protecting yourself from cybersecurity attacks. Some of the ways are listed below.
1) Create a backup of sensitive files.
To prevent losing your data in case of a cyber-attack, you must create backups of your files that are the most sensitive. If you have a backup with you, you will be able to access your data even if it gets stolen.
Regularly backing up your files will help you stay protected from attacks. Even if someone steals your data, they won’t be able to extort money from you to allow you to have it back.

2) Don’t go to malicious websites.
Stay away from sites that don’t begin with ‘https:// ‘as they are the indication that a site is safe to be visited. Another way to know whether a site is safe or not is to check whether there is a lock symbol at the top left corner of the search bar. If the webpage has the lock symbol, it means that you can use it safely.
3) Don’t open suspicious emails.
Email attachments sent by hackers can contain viruses that will breach your security walls and steal your sensitive data. If you receive such emails, delete them immediately to prevent your data from getting stolen.
4) Update the software of your devices.
The ‘bug fixes’ that come with software updates contain important security fixes that will prevent hackers from accessing your sensitive data. Running a device on old software will make it easier for attackers to breach through security loopholes.
These precautions are necessary to protect your devices from cyberattacks. With the rapid progress in technology, your devices also need to stay updated to effectively stay protected from cyber threats.
Cybersecurity Jobs
The career prospects in Cybersecurity are vast, and an increasing number of individuals are exploring that angle. If you want to build a cybersecurity career, this is the right time as a lot of companies are willing to spend millions annually on cybersecurity technicians, analysts, coordinators, and supervisors.
A question that comes to the mind of many people is who needs a job as a cybersecurity professional?
To answer that question, here are some of the points that you can go through to understand which type of people can be benefitted from a job in Cybersecurity.
- If you are interested in developing codes and working with cyber-security software, a job in cyber-security would be perfect for you.
It will improve your skills and allow you to practice on a larger scale. Instead of developing codes for you, you can do that for large companies and earn a good amount of money in return.
- Cyber-security can be pursued by beginners because it is easy to understand. So, even if you don’t have prior knowledge about cyber-security principles, you can start fresh. This is the only stream in IT that allows beginners a fair chance to start building their career in Cybersecurity.
- It is beneficial for both beginners and professionals because of the level ground of play that it offers. So, if an IT professional wishes to improve his career position, he/she can opt for Cybersecurity.
- If you have some basic knowledge of cybersecurity principles, then you will easily be able to get the hang of Cybersecurity. Receiving prior training before starting is recommended because you would get an idea about how the job is going to turn out for you.
- Being adapted to face challenges and adapting to them quickly is the main requirement of a cyber-security professional. You need to have fast responses to effectively thwart a data breach attempt. The job specification of any cybersecurity professional is to be constantly alert because threats don’t come invited.
Cybersecurity Certifications
Cybersecurity certifications will allow you to get employed as a cybersecurity professional. Having a normal bachelor’s degree is not sufficient as it is not enough to equip you with the necessary skills.
To have a successful career in cybersecurity firms, you need to have a cybersecurity degree. The cybersecurity degree requirements vary from certification to certification. Some of the degrees have no requirements, while others need some years of experience.
There are different degrees or certifications that you can pursue to get employed as a cybersecurity professional. Here is the cybersecurity career path explored.
CompTIA Security+ Certification
The CompTIA Security+ certification is for beginners who want to explore the world of IT security. It serves as the entry point to cyber-security certification. The best thing about this certification is that it covers both practical and theoretical studies for the overall growth of a person as a cybersecurity consultant.
After getting a CompTIA Security+ certification, you will be able to use your knowledge to counter security attacks on organizations. Risk management is a core area of this certification, and it equips individuals with the knowledge to minimize risks in an IT framework.
1) The Ethical Hacking Certification
This has become popular in recent times. With this certification, you are taught to think and act from the point of view of a hacker. You would have to breach security barriers to test their resistance to cyber-attacks.
Identifying loopholes in IT systems and applying effective measures to resolve those issues is the main purpose behind ethical hacking. For an impressive cybersecurity career, this certification is essential.
If you want to follow the path of IT security auditor, then you would need this certification as it would enable you to work as a system auditor. You would gain expertise in handling security control and managing vulnerabilities.
The CISSP certification is an expert-level credential. It is meant for those professionals who are seeking expert-level knowledge on operations security, network security, or development security. It will enable you to apply for top positions as an IT security professional.
This is the master level of cybersecurity certifications and enables you to gain expertise in risk management, security operations, IT security regulations, and much more. It is a globally accepted certification and focuses on global security management.
Suggested Read - Top Career Benefits of CISSP Certification
Why are Cybersecurity Certifications Important?
Earning a cybersecurity certification will allow you to specialize in a particular domain of Cybersecurity. Companies are looking for specializations and searching for individuals who can effectively resolve cybersecurity threats by applying their learned skills.
Cybersecurity courses with the best cyber security certifications are widely available across the globe with suitable options. The cybersecurity classes can be attended to obtain training in cybersecurity principles.
If you don’t want to go to any classes, you can get a degree at home by getting a cybersecurity degree online. To prepare for a cybersecurity degree, you can also take the help of good-quality cybersecurity books that will give you basic and advanced knowledge on various domains.
Read - Best Cyber Security Certifications in 2020
Is a cybersecurity degree worth it?
A cybersecurity degree is worth it as it would make your career smooth and progressive with a high-paying cybersecurity degree salary.
A cybersecurity bachelor’s degree is also good enough if you are beginning your career in this sector.
Cybersecurity Job Roles
If you have a cybersecurity certification, getting a cybersecurity degree job would be easy enough for you as there are plenty of opportunities in this sector. Let’s look at some cybersecurity degree jobs.
Cybersecurity Engineer
A cybersecurity engineer is entrusted with the job of creating fool-proof software that will protect the systems from cyber-attacks. The cybersecurity engineer's salary stands at nearly $120,000. Designing and developing secure networks is the key role of a cybersecurity engineer.
Cybersecurity Analyst
A cybersecurity analyst will analyze all the possible loopholes that your system might be having and then devises appropriate solutions to protect them.
The average salary of a cybersecurity analyst is $90,000. Cybersecurity analyst jobs are some of the highest-paid jobs in Cybersecurity.
Cybersecurity Architect
A cybersecurity architect will design the cybersecurity frameworks of organizations and implement cybersecurity protocols to safeguard the data from threats.
Cybersecurity Consultant
A cybersecurity consultant will advise companies and individuals on how to protect their data from getting breached. The average salary of a cybersecurity consultant is nearly $95,000.
What Next?
Often, companies neglect their cybersecurity framework because they think that they can do away with it. This is where attackers take advantage of their vulnerability and breach their systems to attack their sensitive data.
The only way to protect from cyberattacks is by creating a strong security system with multiple layers of protection in it. This would ensure that the attackers won’t be able to get past the multiple layers of security.
These layers must be implemented across personal devices like smartphones, PCs, or laptops. Larger organizations must invest properly in cybersecurity to save their data from getting stolen. It is necessary to understand that cybersecurity does not only depend on having a strong defense system.
It also depends on how vigilant you are with your choices and what steps you have taken to make sure that your systems are safeguarded from all harm. Recognizing and identifying cybersecurity threats before they damage your system is really important.
If you want to learn more cybersecurity courses in detail, enroll in the certification program by Sprintzeal and get certified.
Explore: Online cybersecurity courses
To get full details about cybersecurity training and certifications, chat with our course expert.
Subscribe to our Newsletters
Popular Programs
CISSP® - Certified Information System Security Professional
Live Virtual Training
- 4.4 (964 + Ratings)
- 4k + Learners
CISA® - Certified Information System Auditor
Live Virtual Training
- 4.8 (426 + Ratings)
- 9k + Learners
CISM® - Certified Information Security Manager
Live Virtual Training
- 4.7 (200 + Ratings)
- 48k + Learners
CCSP® - Certified Cloud Security Professional
Live Virtual Training
- 4.6 (964 + Ratings)
- 25k + Learners
Trending Posts
CISM certification cost details
Last updated on Jul 15 2022
Cybersecurity Strategy: Building a Strong Defense for Business
Last updated on Jul 26 2023
The Future of Online Security: Trends to Watch in 2025
Last updated on Feb 17 2025
How to Become IT Security Expert with CISSP Certification
Last updated on Oct 17 2022
Canva Data Breach: Best Lessons for Users and Businesses
Last updated on Feb 26 2025
Which Certification is best for Cybersecurity?
Last updated on Dec 16 2022
Categories
- Agile Management 54
- AI and Machine Learning 42
- Big Data 53
- Business Management 51
- Cloud Computing 44
- Digital Marketing 56
- Information Security 8
- IT Hardware and Networking 17
- IT Security 103
- IT Service Management 29
- Leadership and Management 1
- Microsoft Program 2
- Other 43
- Programming Language 31
- Project Management 162
- Quality Management 75
- Risk Management 8
- Workplace Skill Building 2
Trending Now
Which Certification is best for Cybersecurity?
ebookTop 5 Compelling Reasons To Get A Cyber Security Certification
ebookHow to Become IT Security Expert with CISSP Certification
ebookTop 20 Reasons You Should Get a CISSP Certification
ebookCISM certification cost and career benefits
ebookWhat is CISSP? – Everything about CISSP Certification Explained
ebookPass CISSP Exam - How to Clear CISSP Exam in First Attempt 2024 (UPDATED)
ebookCISSP Certification – Top 25 Career Benefits in 2024
ebookCybersecurity Strategy: Building a Strong Defense for Business
ebookCyber Attack Statistics and Trends to Know in 2024
ebookUpdated Google Certification Training Course list 2024
ArticleWhich Cybersecurity Certification Should I Get First?
ebookCysa+ certification – Should you get it?
ebookList of Top Security Certifications
ArticleEasiest Security Certification to Get
ebookCybersecurity Fundamentals Explained
ebookISACA Certifications List 2024
ebookCareer Benefits of CISM Certification in 2024
ArticleList of Top Information Security Certifications in 2024
ebookCISM certification cost details
ArticleSafeguarding Digital Domain: 10 Most Common Cybercrimes
ebookMitigate the Cyber-Attack Risks with Best Cyber Security Protocols
ebookCybersecurity Interview Questions and Answers 2024
ebookData Leak - What is it, Prevention and Solutions
ebookTop Cybersecurity Software Tools In 2024
ebookWhat is Cryptography - A Comprehensive Guide
ebookInformation Security Analyst - Career, Job Role, and Top Certifications
ebookCyber Security Analyst - How to Become, Job Demand and Top Certifications
ebookIBM Data Breach: Is IBM Really Breach-Proof?
ArticleWhat is the Department of Defense (DoD) Directive 8140
ebookInformation Assurance Model in Cybersecurity
ebookWhat is Data Security - Types, Strategy, Compliance and Regulations
ebookData loss Prevention in Cyber Security Explained
ebookCybersecurity Controls Explained in Detail
ebookCybersecurity Framework - A Complete Guide
ebookCybersecurity Career Paths Guide
ebookFuture of Cybersecurity - Trends and Scope
ebookScope for Cybersecurity in 2024 - Update for 2024
ebookCyber Security Careers and Outlook - 2024 Guide
ebook5 Cybersecurity Predictions in 2024 - Trends and Challenges
ebookEthical Hacking Career: A Career Guide for Ethical Hacker
ebookApplication Security: All You Need To Know
ebookCybersecurity Roles - Top Roles and Skills to Consider in 2024
ebookHow to Get Cyber Essentials Certified
ebookTop 10 Cyber Security Threats and How to Prevent Them
ebookTop 10 Network Scanning Tools of 2025
ebookCyber Incident Response Plan: A Comprehensive Guide
ebookInformation Assurance Careers - Exploring Career Paths
ebookCybersecurity Mesh Architecture: What It Is and How to Build It
ebookWhat is Threat Modeling? Methodologies, Types, and Steps
ebookWhat is Digital Forensics? Types, Process & Challenges
ebookRecent Cyber Attacks & Data Breaches in 2024
ebookHow to Become an Information Security Analyst Salary, Skills, and More
ArticleList of Top Department of Defense (DoD) Approved 8570 Certification Courses
ebookTop 5 Ransomware Attacks to Watch Out for in 2024
ebookJob Prospects for DoD Certified Professionals: A Pathway to Success in cybersecurity
ebook10 Biggest Data Breaches of the 21st Century
ebookWhat is a Cybersecurity Incident?-Types, Impact, Response Process and More
ebookCyber Security Planning - A Detailed Guide for Risk Mitigation
ebookWhat is Cybercrime? Exploring Types, Examples, and Prevention
ebookCybercrime Impacts On Business: 6 Major Effects
ebook5 Types of Cyber Attacks You Should Be Aware of in 2024
ebookCloud Cyber Attacks: Causes, Types, Prevention and Protection
ebookCloud Malware: Types of Attacks and Security Measure
ebookList Of Top Cybersecurity Threats In 2024
ebookRisk-based Audit Planning Guide for Beginners
ebookDemystifying Cloud-Based Cyber Attacks: A Comprehensive Guide
ebookPrevent Cyber Attacks: Strategies to Protect Your Digital Assets
ebookList of Top 10 Cybersecurity Careers in 2024
ebookTop 20 Cybersecurity Trends to Watch Out for in 2024
ArticleHow to Become Cybersecurity Engineer
ArticleUnderstanding Risk assessment in audit planning
ArticleFundamentals of Risk-Based Auditing: A Strategic Framework
ArticleTop 8 Types of Cybersecurity Jobs and Salary Insights
ArticleA Comprehensive Guide to Building Risk-Based Internal Audit Plan
ArticleRisk-Based Internal Auditing Approaches: 7 Steps to Explore
ArticleCompTIA Security+ 601 vs. 701: Understanding Key Differences
ArticleWhy and How to Perform a Risk-Based Internal Audit
ArticleRisk-Based Auditing Techniques Explained
ebookEthical Hacking Tools: Best Ones for Cybersecurity in 2025
ArticleEvolving Cyber Threats and Vulnerabilities in Cybersecurity Risk Management
ArticleWhat Is Secure Access Service Edge (SASE)?
ArticleHow to Stay Cyber-Secure in Work and Personal Life (Tips and Practices)
ArticleTarget Cyber Attack: Key Lessons from the 2013 Data Breach
ArticleLinkedIn User Data Protection Explained
ArticleCanva Data Breach: Best Lessons for Users and Businesses
ArticleHow Did Capital One Respond to Their Major Cyber Incident?
ArticleWhat Innovative Measures Did Reddit Take to Protect User Data?
ArticleHow Does Slack Respond to Security Challenges?
ArticleTwitch Data Breach: Response, Changes, and Key Takeaways
ArticleGuess What Google Did When a Employee Breached Their Firmware
ArticleWhat Happened When Cisco Faced a Cyber Incident?
ArticleWhat Sony Did to Rebuild Trust After a Major Cyberattack
ArticleHow to Handle a Data Breach? Learn from Microsoft!
ArticleCybersecurity Mesh: A New Approach for Security Design
ArticleHow Target Turned a Cyber Crisis into a Lesson for All
ArticleDropbox Data Breach: What Companies Can Learn from It
ArticleHow JPMorgan Chase Strengthened Security After Facing Cyber Threats
ArticleThe Future of Online Security: Trends to Watch in 2025
ArticleLatest Trends in CyberSecurity
ArticleTop 12 Cyber Security Apprenticeships with High Earning Potential in 2025
ArticleEnhancing Safety and Competence in Today's Workplace
Article















