What is the Department of Defense (DoD) Directive 8140
-
 By Niharika Chaurasia
By Niharika Chaurasia - Published on May 31 2023

Table of Contents
- Introduction
- History and Evolution
- Growth and Impact
- Job Categories in DOD 8140 Approved Certifications
- Top DoD Approved Certifications: Maximize Your Security
- Eligibility for DoD 8140-Approved Certification Courses
- Job Prospects with DoD-Approved 8140 Certification
- Salary Prospects for DoD Certified Professionals
- Future of DoD Directive 8140
- Sprintzeal Cybersecurity Certifications
- Conclusion
Introduction
In our modern, interconnected world, where digital information and technology are integral to national security, the Department of Defense (DoD) recognizes a critical demand for exceptionally skilled cybersecurity professionals.
So, what is DOD Directive 8140? And how it contributes towards cybersecurity workforce framework?
To ensure a standardized approach to cybersecurity training and certification, the DoD presented the DoD 8140 directive. In this blog post, we will explore into the details of DoD 8140, including job categories, approved certifications, and who can benefit from DoD 8140-approved certification courses.
Definition: DoD 8140 also known as DoD Cybersecurity Workforce Framework, is a comprehensive directive that outlines the requirements for cybersecurity professionals working within the DoD. It mainly establishes a standardized framework for organizing, training, and certifying personnel involved in cybersecurity-related functions across different branches of the DoD.
History and Evolution
The roots of DoD Directive 8140 can be traced back to the DoD Directive 8570, which was introduced in 2005. Directive 8570 established baseline certification requirements for personnel engaged in Information Assurance (IA) functions within the DoD.
Over time, as technology advanced and threats evolved, the DoD recognized the need for a more comprehensive framework, leading to the development of Directive 8140.
Growth and Impact
DoD Directive 8140, also known as the DoD Cybersecurity Workforce Framework, has revolutionized the cybersecurity landscape in the Department of Defense. It brings a standardized approach to developing a robust cybersecurity workforce by defining job categories, approved certifications, and eligibility criteria.
Directive 8140 plays a crucial role in equipping the DoD with proficient cybersecurity professionals who can effectively combat the ever-changing threats.
By doing this, the DoD will be able to build and maintain a powerful defence against cyberattacks, protecting vital digital infrastructure. In direct reaction to the constantly changing complexity and diversity of cybersecurity threats, Directive 8140 has continued to grow.
As technology advances, malicious actors also develop new methods to exploit vulnerabilities. Directive 8140 ensures that cybersecurity professionals possess the essential knowledge and skills required to effectively safeguard against these evolving threats.
The Impact of Directive 8140 extends beyond the DoD. Many organizations, including government agencies and private sector entities, have recognized the value of aligning their cybersecurity workforce practices with the DoD framework.
This has led to an increased demand for professionals with DoD-approved 8140 certifications, creating exciting job prospects and career opportunities.
Job Categories in DOD 8140 Approved Certifications
DoD 8140 classifies cybersecurity positions into several categories, known as workforce specialty areas. These categories reflect the diverse range of roles and responsibilities within the DoD's cybersecurity workforce.
Some of the key job categories include:
Information Assurance Technician (IAT): These professionals handle tasks related to system administration, network security, and vulnerability assessment.
Information Assurance Manager (IAM): IAMs oversee the overall information assurance program, manage risk assessments, and ensure compliance with security policies.
Cybersecurity Service Provider (CSSP) Analyst: CSSP analysts conduct incident handling, malware analysis, and cybersecurity assessments.
Cybersecurity Service Provider (CSSP) Infrastructure Support: These professionals manage and support network infrastructure components, including firewalls, routers, and switches.
Top DoD Approved Certifications: Maximize Your Security
Skills To meet the cybersecurity workforce requirements, the DoD has identified specific certifications that align with the various job categories outlined in DoD 8140.The DoD-approved certifications play a vital role in evaluating the knowledge and abilities of cybersecurity professionals. Examples of such certifications include:

It's advisable to refer to the official DoD-approved certifications and guidelines for the most accurate and latest list of approved certifications, as the requirements may change over time.
Eligibility for DoD 8140-Approved Certification Courses
The DoD 8140-approved certification courses are primarily intended for personnel working within the DoD or contractors supporting DoD networks and systems. It involves members of the armed forces, civilian staff personnel, and contractors who are in charge of cybersecurity tasks or who are accountable for the defense of DoD data and systems.
Although the DoD is the major target audience for these certificates, candidates seeking cybersecurity jobs in other industries can benefit from them as well. These qualifications are especially useful for people looking for work with government organisations, defence contractors, or businesses that manage vital infrastructure.
Job Prospects with DoD-Approved 8140 Certification
Here's a tabular presentation outlining some of the DoD 8140-approved certifications and their corresponding job roles:
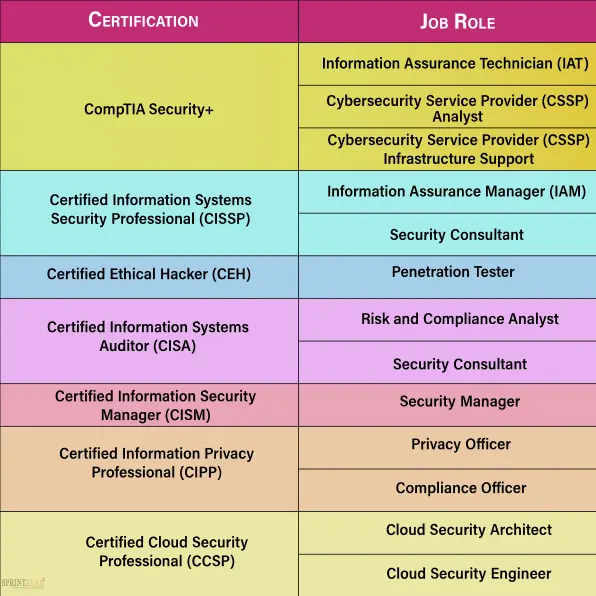
Additionally, there are other DoD-approved certifications and job roles not listed in the table, as the DoD 8140 directive covers a broad range of cybersecurity positions. It's important to research and assess the specific requirements and qualifications for each job role to align your certification goals with your career aspirations effectively.
- Cybersecurity Analyst/Engineer: Responsible for designing and implementing security measures, analyzing threats, and developing incident response plans.
- Security Operations Center (SOC) Analyst: Monitors and responds to security incidents, investigates potential breaches, and implements necessary countermeasures.
- 3. Penetration Tester: Conducts controlled attacks on systems and networks to identify vulnerabilities and recommend security enhancements.
- 4. Security Consultant: Provides expert advice on cybersecurity strategies, risk management, and compliance with regulations and policies.
- Security Architect: Designs and implements secure IT infrastructures, including network architecture, firewalls, and encryption protocols.
- Risk and Compliance Analyst: Ensures organizational compliance with cybersecurity regulations and standards, conducts risk assessments, and develops mitigation strategies.
Salary Prospects for DoD Certified Professionals
DoD certified professionals often enjoy competitive salary prospects due to the critical nature of their roles in national security. According to characteristics including work category, experience, location, and education, salaries can change. The following compensation ranges represent the most current averages for professionals with DoD certifications:
Certified Information Security Manager (CISM)
Earnings for professionals with CISM certification might range from $90,000 to $140,000 annually.
Certified Ethical Hacker (CEH)
A CEH-certified professional can expect to make between $70,000 and $120,000 annually.
CompTIA Security+
Professionals with this credential can anticipate yearly wages between $50,000 and $80,000.
Certified Information Systems Security Professional (CISSP)
The annual salary range for professionals with CISSP certification is between $90,000 and over $155,000.
It's crucial to remember that these compensation ranges are only an estimate and may change depending on things like experience, job type, location, and extra credentials.
Future of DoD Directive 8140
As the cybersecurity landscape continues to evolve, the DoD will adapt Directive 8140 to address emerging challenges and technological advancements. The framework will likely expand to include new job categories and certifications to keep pace with the evolving threat landscape.
Moreover, the DoD's continued emphasis on cybersecurity and the widespread adoption of Directive 8140 by other organizations signal a promising future for professionals with DoD-approved certifications.
Those who possess these certifications will be well-positioned to secure rewarding roles within the DoD, government agencies, defense contractors, and various industries that prioritize cybersecurity.
Sprintzeal Cybersecurity Certifications
Sprintzeal offers well-structured and up-to-date training programs that align with the DoD 8140 requirements. Our courses cover all the necessary concepts and skills needed to excel in the cybersecurity field.
We employ highly experienced instructors who possess in-depth knowledge of cybersecurity and relevant certifications. They provide practical insights and real-world examples to enhance the learning experience.
Sprintzeal's certification courses are widely recognized and accredited. Completing cybersecurity certifications from Sprintzeal enhances the credibility of professionals in the cybersecurity field and opens doors to a wide range of job opportunities.
Conclusion
The Department of Defense's DoD 8140 directive plays a pivotal role in ensuring a skilled and competent cybersecurity workforce within the DoD. The DoD works to maintain a high level of cybersecurity skill throughout its ranks by designating job categories, detailing accepted certifications, and determining qualifying criteria.
In addition to enhancing national security, these efforts provide professionals interested in the cybersecurity industry meaningful job prospects. Investigating the DoD 8140-approved certification courses will help you improve your cybersecurity abilities and boost your career inside the DoD ecosystem if you are an employee of the DoD or a contractor supporting their activities.
Explore courses of Sprintzeal to upskill and advance your career in the dynamic field of cybersecurity. Read more interesting articles of Sprintzeal to add more information to your knowledge in this field. Contact us for any query or assistance.
Subscribe to our Newsletters
Popular Programs
CISSP® - Certified Information System Security Professional
Live Virtual Training
- 4 (964 + Ratings)
- 14k + Learners
CISA® - Certified Information System Auditor
Live Virtual Training
- 4.7 (426 + Ratings)
- 64k + Learners
CISM® - Certified Information Security Manager
Live Virtual Training
- 4 (200 + Ratings)
- 31k + Learners
CCSP® - Certified Cloud Security Professional
Live Virtual Training
- 4.8 (964 + Ratings)
- 48k + Learners
Trending Posts
Top 12 Cyber Security Apprenticeships with High Earning Potential in 2025
Last updated on Mar 31 2025
Canva Data Breach: Best Lessons for Users and Businesses
Last updated on Feb 26 2025
Information Assurance Careers - Exploring Career Paths
Last updated on May 25 2023
How to Become IT Security Expert with CISSP Certification
Last updated on Oct 17 2022
Cyber Attack Statistics and Trends to Know in 2024
Last updated on Aug 9 2023
How to Become an Information Security Analyst Salary, Skills, and More
Last updated on Jun 22 2023
Categories
- Agile Management 54
- AI and Machine Learning 42
- Big Data 53
- Business Management 51
- Cloud Computing 44
- Digital Marketing 56
- Information Security 8
- IT Hardware and Networking 17
- IT Security 103
- IT Service Management 29
- Leadership and Management 1
- Microsoft Program 2
- Other 43
- Programming Language 31
- Project Management 162
- Quality Management 75
- Risk Management 8
- Workplace Skill Building 2
Trending Now
Which Certification is best for Cybersecurity?
ebookTop 5 Compelling Reasons To Get A Cyber Security Certification
ebookHow to Become IT Security Expert with CISSP Certification
ebookTop 20 Reasons You Should Get a CISSP Certification
ebookCISM certification cost and career benefits
ebookWhat is CISSP? – Everything about CISSP Certification Explained
ebookPass CISSP Exam - How to Clear CISSP Exam in First Attempt 2024 (UPDATED)
ebookCISSP Certification – Top 25 Career Benefits in 2024
ebookCybersecurity – Everything You Need to Know About it
ebookCybersecurity Strategy: Building a Strong Defense for Business
ebookCyber Attack Statistics and Trends to Know in 2024
ebookUpdated Google Certification Training Course list 2024
ArticleWhich Cybersecurity Certification Should I Get First?
ebookCysa+ certification – Should you get it?
ebookList of Top Security Certifications
ArticleEasiest Security Certification to Get
ebookCybersecurity Fundamentals Explained
ebookISACA Certifications List 2024
ebookCareer Benefits of CISM Certification in 2024
ArticleList of Top Information Security Certifications in 2024
ebookCISM certification cost details
ArticleSafeguarding Digital Domain: 10 Most Common Cybercrimes
ebookMitigate the Cyber-Attack Risks with Best Cyber Security Protocols
ebookCybersecurity Interview Questions and Answers 2024
ebookData Leak - What is it, Prevention and Solutions
ebookTop Cybersecurity Software Tools In 2024
ebookWhat is Cryptography - A Comprehensive Guide
ebookInformation Security Analyst - Career, Job Role, and Top Certifications
ebookCyber Security Analyst - How to Become, Job Demand and Top Certifications
ebookIBM Data Breach: Is IBM Really Breach-Proof?
ArticleInformation Assurance Model in Cybersecurity
ebookWhat is Data Security - Types, Strategy, Compliance and Regulations
ebookData loss Prevention in Cyber Security Explained
ebookCybersecurity Controls Explained in Detail
ebookCybersecurity Framework - A Complete Guide
ebookCybersecurity Career Paths Guide
ebookFuture of Cybersecurity - Trends and Scope
ebookScope for Cybersecurity in 2024 - Update for 2024
ebookCyber Security Careers and Outlook - 2024 Guide
ebook5 Cybersecurity Predictions in 2024 - Trends and Challenges
ebookEthical Hacking Career: A Career Guide for Ethical Hacker
ebookApplication Security: All You Need To Know
ebookCybersecurity Roles - Top Roles and Skills to Consider in 2024
ebookHow to Get Cyber Essentials Certified
ebookTop 10 Cyber Security Threats and How to Prevent Them
ebookTop 10 Network Scanning Tools of 2025
ebookCyber Incident Response Plan: A Comprehensive Guide
ebookInformation Assurance Careers - Exploring Career Paths
ebookCybersecurity Mesh Architecture: What It Is and How to Build It
ebookWhat is Threat Modeling? Methodologies, Types, and Steps
ebookWhat is Digital Forensics? Types, Process & Challenges
ebookRecent Cyber Attacks & Data Breaches in 2024
ebookHow to Become an Information Security Analyst Salary, Skills, and More
ArticleList of Top Department of Defense (DoD) Approved 8570 Certification Courses
ebookTop 5 Ransomware Attacks to Watch Out for in 2024
ebookJob Prospects for DoD Certified Professionals: A Pathway to Success in cybersecurity
ebook10 Biggest Data Breaches of the 21st Century
ebookWhat is a Cybersecurity Incident?-Types, Impact, Response Process and More
ebookCyber Security Planning - A Detailed Guide for Risk Mitigation
ebookWhat is Cybercrime? Exploring Types, Examples, and Prevention
ebookCybercrime Impacts On Business: 6 Major Effects
ebook5 Types of Cyber Attacks You Should Be Aware of in 2024
ebookCloud Cyber Attacks: Causes, Types, Prevention and Protection
ebookCloud Malware: Types of Attacks and Security Measure
ebookList Of Top Cybersecurity Threats In 2024
ebookRisk-based Audit Planning Guide for Beginners
ebookDemystifying Cloud-Based Cyber Attacks: A Comprehensive Guide
ebookPrevent Cyber Attacks: Strategies to Protect Your Digital Assets
ebookList of Top 10 Cybersecurity Careers in 2024
ebookTop 20 Cybersecurity Trends to Watch Out for in 2024
ArticleHow to Become Cybersecurity Engineer
ArticleUnderstanding Risk assessment in audit planning
ArticleFundamentals of Risk-Based Auditing: A Strategic Framework
ArticleTop 8 Types of Cybersecurity Jobs and Salary Insights
ArticleA Comprehensive Guide to Building Risk-Based Internal Audit Plan
ArticleRisk-Based Internal Auditing Approaches: 7 Steps to Explore
ArticleCompTIA Security+ 601 vs. 701: Understanding Key Differences
ArticleWhy and How to Perform a Risk-Based Internal Audit
ArticleRisk-Based Auditing Techniques Explained
ebookEthical Hacking Tools: Best Ones for Cybersecurity in 2025
ArticleEvolving Cyber Threats and Vulnerabilities in Cybersecurity Risk Management
ArticleWhat Is Secure Access Service Edge (SASE)?
ArticleHow to Stay Cyber-Secure in Work and Personal Life (Tips and Practices)
ArticleTarget Cyber Attack: Key Lessons from the 2013 Data Breach
ArticleLinkedIn User Data Protection Explained
ArticleCanva Data Breach: Best Lessons for Users and Businesses
ArticleHow Did Capital One Respond to Their Major Cyber Incident?
ArticleWhat Innovative Measures Did Reddit Take to Protect User Data?
ArticleHow Does Slack Respond to Security Challenges?
ArticleTwitch Data Breach: Response, Changes, and Key Takeaways
ArticleGuess What Google Did When a Employee Breached Their Firmware
ArticleWhat Happened When Cisco Faced a Cyber Incident?
ArticleWhat Sony Did to Rebuild Trust After a Major Cyberattack
ArticleHow to Handle a Data Breach? Learn from Microsoft!
ArticleCybersecurity Mesh: A New Approach for Security Design
ArticleHow Target Turned a Cyber Crisis into a Lesson for All
ArticleDropbox Data Breach: What Companies Can Learn from It
ArticleHow JPMorgan Chase Strengthened Security After Facing Cyber Threats
ArticleThe Future of Online Security: Trends to Watch in 2025
ArticleLatest Trends in CyberSecurity
ArticleTop 12 Cyber Security Apprenticeships with High Earning Potential in 2025
ArticleEnhancing Safety and Competence in Today's Workplace
Article
















